Privacy for Sale
Your privacy is being attacked yet again as the bill passes to allow the sale of your browsing history.
Check out the Senate roll call list and the House list to see where your representatives stood on the issue.

Your privacy is being attacked yet again as the bill passes to allow the sale of your browsing history.
Check out the Senate roll call list and the House list to see where your representatives stood on the issue.

Fascinating look inside Def Con.
“When I received my press credentials for the convention, they came with a warning that all WiFi networks at the convention and in nearby hotels should be considered “extremely hostile,” which was to be expected at a hacker convention.”
How often do you use your email? Your Twitter / Facebook / other social media accounts? Your cloud apps? What would you do if you lost it all? What is recovering it worth to you?
When we have something of value, it becomes a target. And, the more we entwine our lives with technology, the more valuable those 1s and 0s become to us.
Though cyber extortion is not new, it is interesting how common it is becoming.
The latest attempt I recently read involved the loss of the @N twitter handle, which was facilitated by both PayPal and GoDaddy.
Then there is the case of Hunter Moore who was arrested and indicted by the FBI for his involvement in hacking private email accounts to gain access to explicit pictures that were meant for private use only. While this was not exactly extortion, it was a method of hacking and stealing of personal digital property that was used to shame and make money off of unsuspecting people.
Last year the story making the rounds was about Cryptolocker hijacking people’s data and then requiring money to unlock it and regain access to it.
Then there was of course the great Facebook, Gmail, Twitter hack I wrote about in December.
This is by no means an exhaustive list, rather just one to show the different ways your data can be used against you.
What does this all mean for you? It should heighten your awareness of cyber security and the very real threats that exist out there today. How do we mitigate these threats? We do what we can to protect our data. Following is a simple list of steps you can take immediately to avoid becoming a victim.
This means not only data you physically have access to like your financial documents, family photos/videos, or your music – but also your online presence. Many social networks let you download the entire contents of your user profile. You should also consider redundant backup options such as physical backups and off site backups. Just remember to make sure both are secure.
Facebook, Gmail, Twitter, Paypal and more utilize 2-factor authentication. My first introduction to this was using an authenticator for my World of Warcraft account, which I opted for as soon as they were made available. I still use 2-factor on that account today. This Life Hacker article has a great rundown of all the places you should enable it. Do it now!
While sites may require you to provide a birthday or email address, the also usually give you the ability to keep this information private. Those who need to know the year you were born or your private email address already have that information or can ask for it. There is no need for it to be out in the open for everyone to see. Also, don’t let sites save your credit card information. While it is an added convenience, as the case of @N above demonstrates, it can be used against you. Other advice he offered in his article was to call your institutions and require them to NOT share any of your personal information over the phone. That means birth dates, names, or partial information like last 4 of social or credit cards.
This may sound odd as the whole allure of the internet is connecting with strangers. However, if you don’t know someone, you should be very cautious about letting them into any social network circle where they can find out more information about you as this can be used against you.
Don’t click on anything you can’t easily identify. Don’t submit information to sites you are not familiar with. Don’t trust things just because they come from people you know. Don’t download things to your computer without some sort of software protection installed.
In summary, treat your digital property much like you would treat your physical property. Follow the Hide Lock Take philosophy. It works for both your email and your car.
Being the 2-factor security person that I am, I know many of you have probably read about Facebook, GMail, and Twitter passwords being hacked. Though you can’t do much about that (other than not have accounts with those services of course), there are steps you can take to keep those accounts secure even if someone else has your password. All that is required is that you have a mobile phone and that you set it up from your computer (I don’t know of a way to do this from the mobile side only).
Facebook:
Facebook users, to enable the 2-factor setting click on the lock icon and click on the link at the bottom that says “See more settings”.
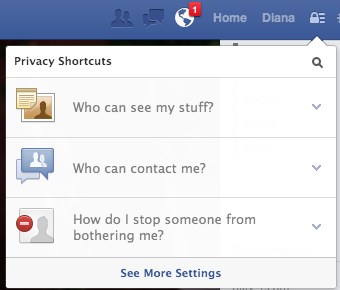
Once there, click on the Security link 2nd from the top on the left.
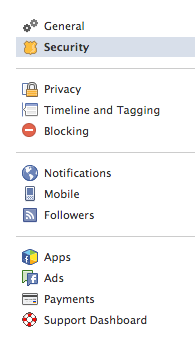
Then click on Login Approvals.
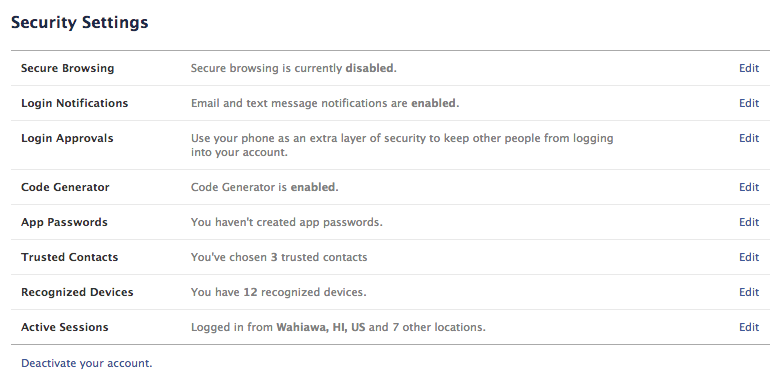
There you will be given a checkbox to “Require a security code to access my account from unknown browsers”.
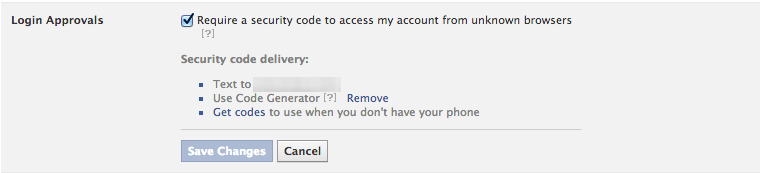
You can check that box and then choose which method you use to get your codes. I chose the code generator because that will work even if I only have access to WiFi, whereas receiving a text message may not. I would also at this time generate extra codes just in case you lose your phone. Save them in a place that will be easy to access, so you can get back to your account easily should you need to.
While you’re in the security section I would also suggest you check the active sessions and recognized devices. End activity on anything you don’t recognize. Lastly, setup your trusted contacts. Be sure to choose people who actually use Facebook regularly.
GMail:
GMail users who use their accounts on multiple devices may find this method a bit cumbersome, but it’s only cumbersome to setup. Once it’s done, you don’t have to make any changes unless you get a new device or wish to disable it.
Login to your GMail account and then find the cog icon under your picture on the upper righthand side of your screen and click settings.
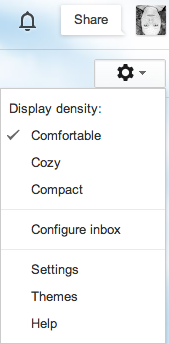
Once there, click Accounts at the top and you will find security settings.
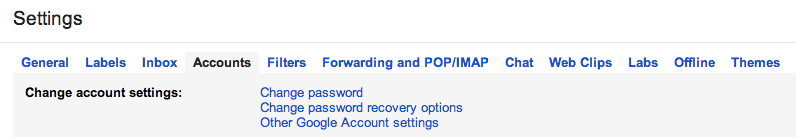
Clicking Account Recovery Options lets you set up your phone to use to recover your account should you forget your password or to challenge hackers. You can also add a recover email address as well as an alternate email address you can log in with. I would highly suggest doing both.
Clicking Other Google Account Settings will take you to a page that lists all of the settings for your Google identity. If you’ve never been here, I suggest you read it so that you understand more about the way Google views & uses your information. For our purposes today, click on Security from the menu on the left.
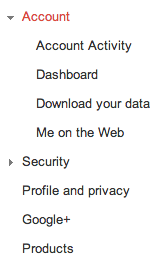
From there, scroll down to the bottom to find 2-Factor Authentication and turn it on.
After you set it up, you will want to create device / application specific passwords for your account so that you can log into your email through your phone, tablet, or other device that doesn’t use 2-factor authentication. You can click on the link visible in the screen shot above to get there.
Pro-Tip, you can use one generated password for all of your devices if you enter it into all of them at the same time. Caution though, if you do that and have to revoke it for some reason (you lose your phone), you’ll end up revoking it for all devices instead of just that one.
Twitter:
Login to Twitter and click the cog icon on the top right hand side of the nav bar.
Then select settings from the menu.
Then select Security and Privacy from the menu on the left.
Then select one of the two login verification options available.
Hopefully this was helpful to some of you. I know these settings can seem buried and intimidating if you’ve never used them before, but I suggest it is worth it to go through all of this trouble so that you don’t end up losing your digital life to someone else’s malicious activities.
Censorship Quotes by Literary Authors
“I am against censorship. In all forms. Not just for the right of masterpieces ”high art” to be scandalous.
But what about pornography (commercial)?
Find the wider context:
notion of voluptuousness la Bataille?
But what about children? Not even for them? Horror comics, etc.
Why forbid them comics when they can read worse things in the newspapers any day. Napalm bombing in Vietnam, etc.
A just/ discriminating censorship is impossible.”
I do not have many words to add to the multiple that are already out there. What I do have to say is that about a year ago I was protesting SOPA with the rest of you. It was one of those things those of us who care so deeply about freedom and the Internet did in hopes that it would actually bring about change.
Internet and Information freedom are near and dear to my heart. My entire Masters research was on FOSS / Fedora. I’ve posted on this blog about many of the things that are threats to this freedom including cyber bullying, censorship, and net neutrality.
Though I have a few papers floating around on the Internet, you will not find any of them in a journal much to the dismay of many of you who have contacted me for copies and citations. Why? Because I refuse to have my research (especially that which I do of my own free will and with no outside funding) published in a journal that cannot be accessed by the public, even if this hurts me academically.
I am not the only one that has a problem with the journal system and there are a few journals out there that have risen up against the status quo. There are also a few people who have taken a stand against the privatization of publicly funded information. Aaron Swartz was one such person. While he should be remembered for the many awesome things he did for Internet and Information Freedom, it is the ending of his life over the weekend that is being talked about today.
All I can say is the world, especially those of us who feel the same way he did, lost a great mind and advocate. He has been an inspiration to many of us, and he will only continue to do so. It will be interesting now to see how he has changed the world through the ending of his own. I am just an academic and a wanna-be hacker, but I will always do what I can to fight many of the same fights he did.
In the words of famed anthropologist Margaret Mead:
Never doubt that a small group of thoughtful, committed citizens can change the world; indeed, it’s the only thing that ever has.
How are you changing the world today?
P.S. If you are reading this through an RSS feed – thank Aaron…
Well, it looks like I’m SXSW bound yet again this year. Still trying to find a hotel as they are all sold out and I was late to sign up – but that’s another story entirely!
While at SXSW this year I hope to not only enjoy a lot of great panels, but also recruit some of the top speakers and participants I find there to hopefully contribute to and collaborate in a virtual barcamp community I’m helping to launch. (There may even be a private rooftop party at SXSW for the chosen few *hint hint*).
If you’re a technologist who would like to connect with your peers, share your knowledge, and learn from others through teleconferences where you choose the topics to speak on and/or choose from a list of sessions led by others you wish to participate in, please contact me (diana [at] cyber-anthro.com)! We need thought leaders on all subjects who aren’t afraid to share their knowledge with the masses. Each conversation will be recorded and then posted as a podcast on our site to be shared with anyone who wishes to listen.
There is no catch to being a part of this community other than you have to participate! Only those who wish to participate in leading or joining in these conversations need apply. That said, this service will not only be free to all participants, but it will also all make all recorded sessions available to the public.
That means if you just want to listen, there is no need to join! You can visit the site, or follow the RSS/Twitter feed to hear the latest and greatest discussions on tech today. So, if there is someone you think would be great at leading and/or participating in these tech conversations, I need you to please send them my way. Otherwise, there will be no one to listen to and that just wouldn’t be any fun now would it.
I’m really hoping people in the Open Source and Fedora communities will step up and participate. This is not only a great way to get your voice heard, but it is also a great way to talk about the projects you participate in and may even help to get the word out to get other developers to join your cause.
Lastly, this isn’t just for developers. If you’re a scripter, coder, designer, or usability professional we need your voices too! The goal is to have thought leaders in all aspects of technology connecting, sharing, and learning through live audio conversations and collaborations.
We figure barcamps are very cool, but they are limited to the geographic area in which they are held. So, why not find a way for people from all over the world to participate in one without ever having to leave their desks.
I’m really stoked about this unique opportunity to bring people together from around the world to have live conversations with one another about all the wonderfully awesome things that are going on in tech today. I’m even more excited that these conversations will then be made available for FREE to anyone who wishes to listen and learn something.
If you’re willing to speak on something as early as next week and you have the perfect topic in mind (and perhaps know of a few people that can jump in on the conversation with you), I need you to contact me ASAP (diana [at] cyber-anthro.com)! We are still in the very early stages of getting the site up – but I need content to make it happen, so I need people now (who aren’t afraid to work through a few bugs with me) to help me get this going.
I look forward to hearing from you!
From a direct email Best Buy sent me:
“Next time you’re at a Best Buy store you can conveniently get the product information you need right from your mobile phone. Learn more about specifications, ratings and reviews using the new QR Mobile Code Reader APP.
From a post I made December of 2008:
Two ads come to mind immediately of stores mentioning how they provide access to a computer right in the store in order to research the product and their competitors prices. I think though, that they should take this one step further, why not offer an in store wireless connection that mobile phones can use to do the research with. Through that connection offer a ‘homepage’ or default page that comes up when they go to connect with all of the in-store specials. These specials then list not only the store’s price, but also their competitors online prices as well as specs, compatibility, and upgrade information about the product itself.
While yes, I agree that few people will use this in the beginning, but imagine those people then SHARING that information with the people around them. Then those people the shared it with learning of it, using it, and then sharing it with others too. It’s an in store marketing device, one that they are already providing through the use of an in store computer, but one that is a bit more private and a hell of a lot more useful than most sales people.
This can then be extended even further than that — say using a barcode scanner or photo recognition software. Just imagine the possibilities when you put access to pertinent information in the palm of a consumers hand.
One example would be utilizing Target’s Amazon relation ship by putting URLs on the tags for all the electronic items in the store. Here I can go an extra step and actually read the reviews for the item I’m looking to purchase. I not only get to look up prices, specs, and other important information, but I also get to see what OTHER people think of the product too. Then, if I purchase it in store I can say perhaps get $5 off my next Amazon or Target purchase if I leave a review thus perpetuating the cycle.
Someone should pay me to come up with this stuff. I come up with these sorts of ideas all of the time!
(Yes this is a repost as I realized recently I had copied out the wrong paragraph from the BB email!)
So did the rest of the world, and a few sites are blogging about the reasons why. See the links below for more details.
FastCompany: Facebook and Twitter Attacks Were Political, and Personal
ZDNet: Did Russians attack Twitter over pro-Georgian blogger?
PCWorld: Twitter DDoS Attack Politically Motivated, Says Report
This semester I am taking Design Anthropology. I took this class as an undergrad and it is one of the reasons why I chose to pursue my masters in anthropology. The experience in working with a tech company, in both cases Motorola, on a real research issue where we go out and do field work and then as a class analyze the data, is simply amazing. This semester we researched how people extend their experiences through second screens or mobile devices.
I spoke at the beginning of the semester about how I use my iPhone (and previously Blackberry and before that Treo – I’ve had a smart phone since 2002). Several of the things I do include using it to share my immediate experience with my friends such as picture blogging (Twinkle for Twitter and Flickr to Livejournal), actual blogging, looking up information for class while listening to the lecture and participating in the discussion, and researching products in stores while in the store. This is all in addition to checking my email, chatting, texting, playing games (Spore at the moment), reading blogs, and using many other programs. The class looked back at me as if I was an alien. Most use their phone only for talking or at most texting. So, I made it my mission to actually find someone to do my fieldwork on that did the same thing I did.
And I did! I chose First Saturday, a tech swap meet, to do my research. I knew I’d find SOMEONE that did what I did there. And sure enough, my partner and I spotted someone at about 3am trying to buy a Macbook. What we found out was that during the half hour we observed him he used three phones, 2 Blackberries and 1 iPhone, to chat with his partner who was there with him (he had one Blackberry), look up prices, research the product itself, and research a technical problem the Macbook was experiencing. Aha! I am not the only one! This does, however, bring me to an interesting trend – on the spot researching, and stores seem to be cashing in on it.
Two ads come to mind immediately of stores mentioning how they provide access to a computer right in the store in order to research the product and their competitors prices. I think though, that they should take this one step further – why not offer an in store wireless connection that mobile phones can use to do the research with. Through that connection offer a ‘homepage’ or default page that comes up when they go to connect with all of the in-store specials. These specials then list not only the store’s price, but also their competitors online prices as well as specs, compatibility, and upgrade information about the product itself.
While yes, I agree that few people will use this in the beginning, but imagine those people then SHARING that information with the people around them. Then those people the shared it with learning of it, using it, and then sharing it with others too. It’s an in store marketing device, one that they are already providing through the use of an in store computer, but one that is a bit more private and a hell of a lot more useful than most sales people.
This can then be extended even further than that – say using a barcode scanner or photo recognition software. Just imagine the possibilities when you put access to pertinent information in the palm of a consumers hand.
One example would be utilizing Target’s Amazon relation ship by putting URLs on the tags for all the electronic items in the store. Here I can go an extra step and actually read the reviews for the item I’m looking to purchase. I not only get to look up prices, specs, and other important information, but I also get to see what OTHER people think of the product too. Then, if I purchase it in store I can say perhaps get $5 off my next Amazon or Target purchase if I leave a review thus perpetuating the cycle.
Nintendo sees the light letting you download demos of games right to your DS in some stores. Bookstores should jump on that letting you read reviews of the latest releases right on your mobile device, or go one step further by allowing you to download ebooks/zines after checking out the real thing. Giving people access right in the store to information as well as reviews and then allowing them to EASILY share their experience with others is, in my humble opinion, one of the great ways to bridge the gap between the brick and mortar stores and their thriving digital counterparts.
The trend has already begun. Stores are already giving people access to computers right there in the store to do this – it’s time someone started taking just a bit further.
/end being a dork, usability junky and ex advertising agency information architect…
p.s. My chapter for our report to Motorola is on Complex Multiple Engagements – think of it as an analysis of our observations on how people strive to do things simultaneously or in quick succession through the use of technology – then design implications based on my analysis of these observations.
Keep up with Twitter’s election feed here.
Facebook’s ticker is here.
MySpace election page is here.
YouTube’s election page is here.
See Google’s elections maps here.
CNN’s political ticker is here.
MSN’s election page is here.
NYT’s election page is here.
The Guardian’s election page is here. (if you want a British perspective)
Have one to add? Leave a comment!
Chevron has joined forces with the Economist Group to bring you Energyville, your very own city where you get to manage the energy consumption while keeping your people “prosperous, secure, and living in a clean environment”.
It sounds pretty interesting and reminds me, a bit on the surface at least, of Sim City. It even makes me think of Jane McGonigal’s a World With Out Oil, if only because of the subject matter.
I may suggest that if you are interested in taking up the challenge of Energyville you watch the Story of Stuff first. I think the two might go well hand in hand.